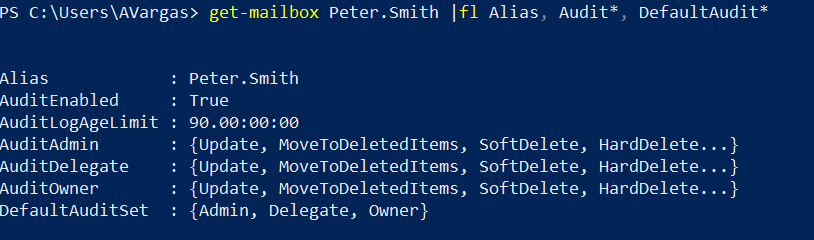
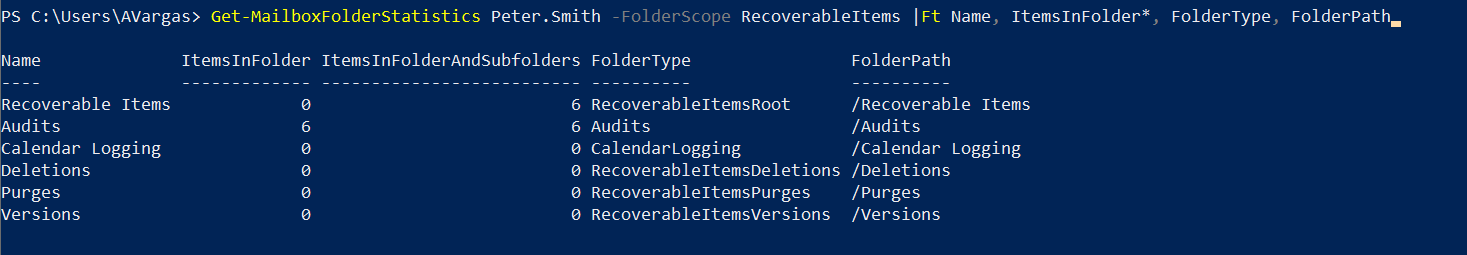
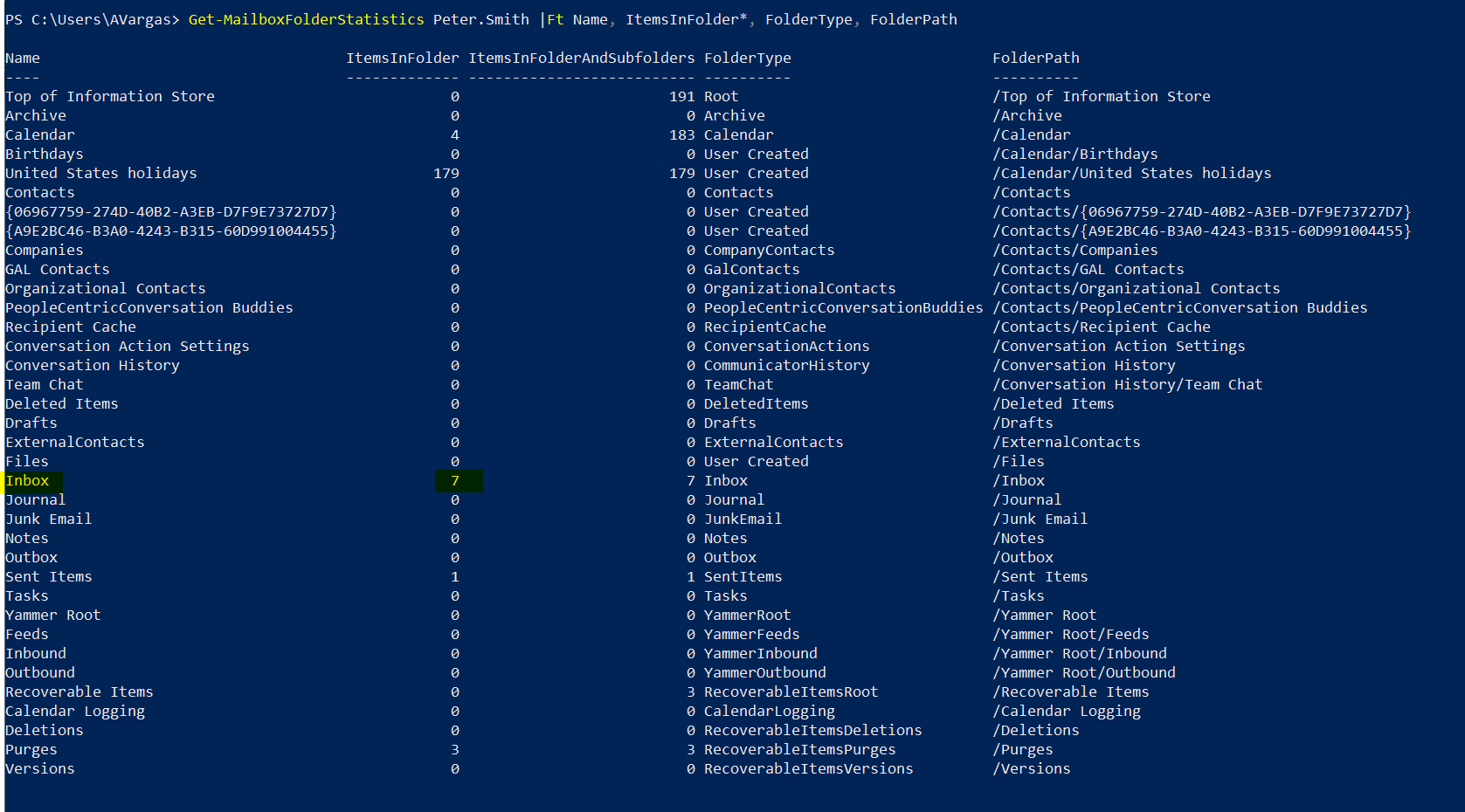
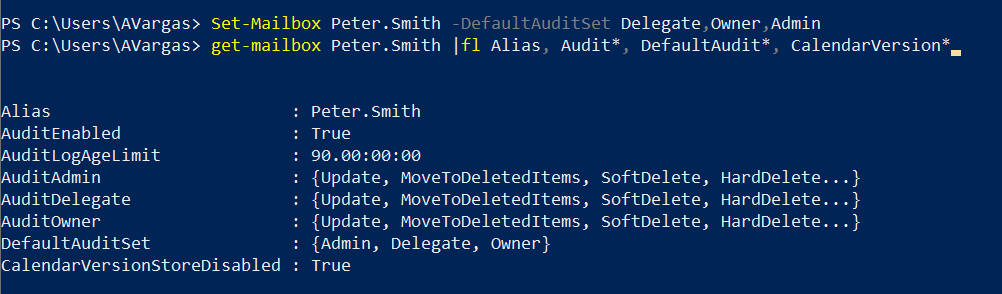
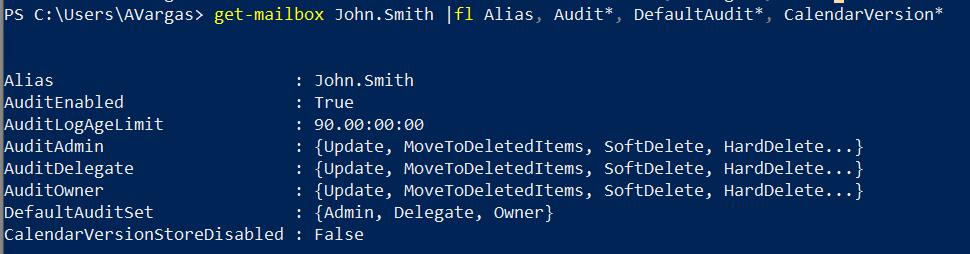
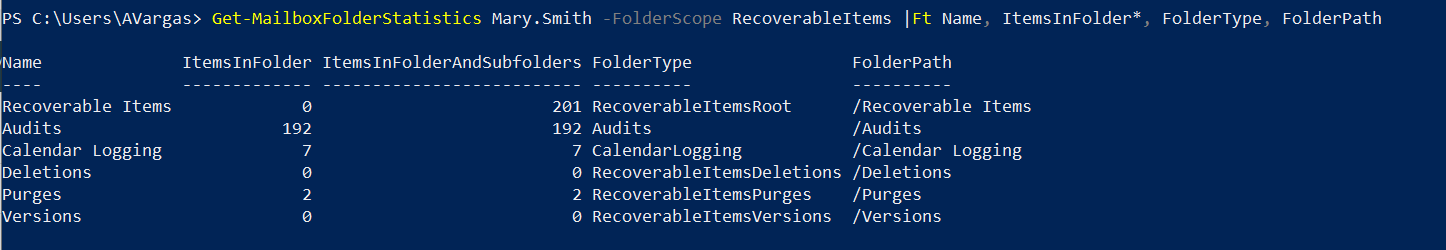
Note: Let me start with a quick note. This blog post was initially drafted to include multiple mail flow coexistence scenarios, between two Office 365 tenants. While I was writing the first scenario, I realized that it was so extensive that it didn’t make sense to put more scenarios in the same post. So stay tuned for more posts, each with its different scenario and some more focused on tenant to tenant enterprise migrations and mail flow during a coexistence period. Enjoy!
Some context
Microsoft tenant to tenant email migrations are very common in our days, and if some are small in terms of users, and the option is to just move them all at the same time, some are too big to have that approach.
Would you consider moving 50 thousand user mailboxes, in one single cut over batch, from one Exchange Online tenant to another? Probably not.
And there’s several reasons not to consider it, most, if not all of them having the user experience in mind. It’s not just about how many terabytes you can move per day, it’s also about re configuring Outlook profiles, re doing the Exchange partnership connection in your phone, all other Office 365 workloads, etc.
So when a cut over is not being considered, the coexistence between tenants comes into play. The biggest question is, can I leverage the same email domain in two tenants? And technically the answer is yes you can, but you’ll need an address rewriting service help you do it.
In a context of a migration, address rewriting is not all you need to have mail flow coexistence, but it’s the key component.
There are other components for you to consider, when doing tenant to tenant with coexistence, but this blog posts series will be focused on mail flow.
What do you need and why should you do it versus hosting it?
Lets address the requirements first. Assuming of course you have 2 tenants, the source and destination or in some cases just two tenants from which you want to send and receive email from, using a single SMTP domain, what you need next is something to do address rewriting (outbound email) and conditional forwarding or address rewriting (inbound email).
I will use the Microsoft Exchange Edge server. It’s a reliable service, that can be designed and implemented as high available and redundant, and it has a very easy to configure bidirectional address rewriting agent.
Note: before reading the rest of this blog post, I highly recommend that you click on the link above and read all details about how the Exchange Address Rewriting works.
Now lets address why should you do it yourself vs hosting it. In fact I think the decision is up to you, but there’s two things you should strongly consider:
- Do you want to pay a per user fee to host a service to either a migration software company or an email relay company, when you can do it yourself at much less cost?
- More importantly, will you allow a third party company into a crucial part of your email flow pipeline?
Those two questions are relevant, specially the second one. It involves SLAs and other super important things to consider, specially in the Enterprise space.
But if the answer to both questions above is yes, then you’re covered. If not, continue reading.
What will this blog post cover
This blog post will address a first scenario detailing mail flow simple coexistence with two tenants using one single email domain. I am labeling it as scenario 1, because this is the first blog post of a series that will cover other scenarios.
Scenario 1: Share a same email domain between two Exchange Online tenants
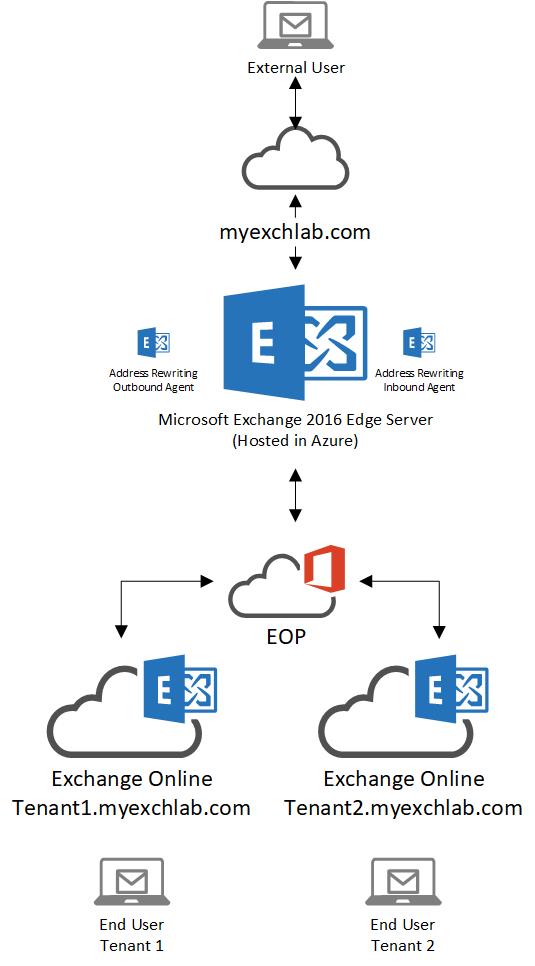
What are the requirements?
To set the scenario above you need the following:
- Two Exchange Online tenants (of course!)
- One unique vanity domain per Office 365 tenant, which in my cases is:
- Tenant1.myexchlab.com
- Tenant2.myexchlab.com
- One vanity domain to be shared by the two tenants, which in my case is myexchlab.com
- At least one Microsoft Exchange Edge Server
- An SSL certificate to encrypt mail flow between both Exchange Online tenants and the Microsoft Exchange Edge
Some important notes about the requirements:
- my tenant vanity domains are sub domains of the shared vanity domain, but that is not a requirement. You can use different domains (i.e abc.com and xyz.com) in your configuration.
- In this scenario all outbound and inbound mail flow goes via the Edge server. It is highly recommended that, for production purposes, you set up a high available and redundant multiple Edge server infrastructure.
- My Edge Server is hosted in Azure, because it’s convenient for me to quickly set it up. You can host yours anywhere you want.
- The SSL certificate and using TLS between the Exchange Online tenants and the Edge Server, is optional but recommended.
Outbound email from Office 365
In this scenario both tenants send all email via the Edge server. Optionally you can configure Conditional Mail Routing in Exchange Online, if you want just a group of users to route their email via the Edge. I am not going to detail that here, but please reach out if you need to elaborate more on that option.
Create the send connector in Exchange Online
First lets check how the connector in Office 365 is created. If you need any basic help on how to set up Exchange Online connectors, read this.
- In the select mail flow scenario, select the source as “Office 365” and the destination as “Partner Organization”
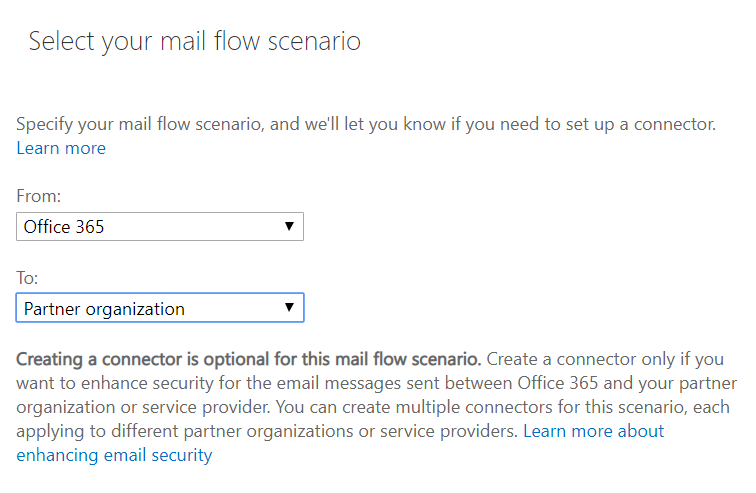
- Name the connector and turn it on
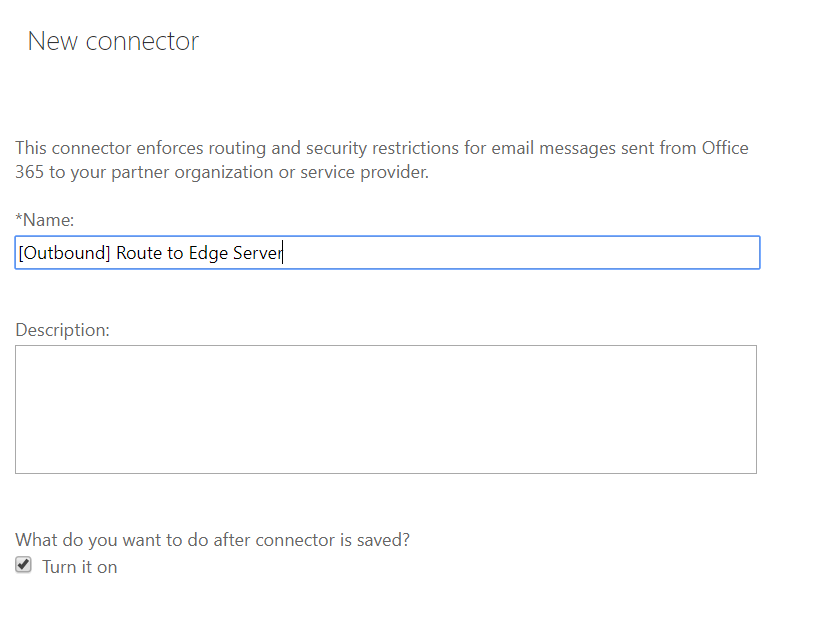
- Select the destination email domains. I have selected * which means this connector applies to all external email domains
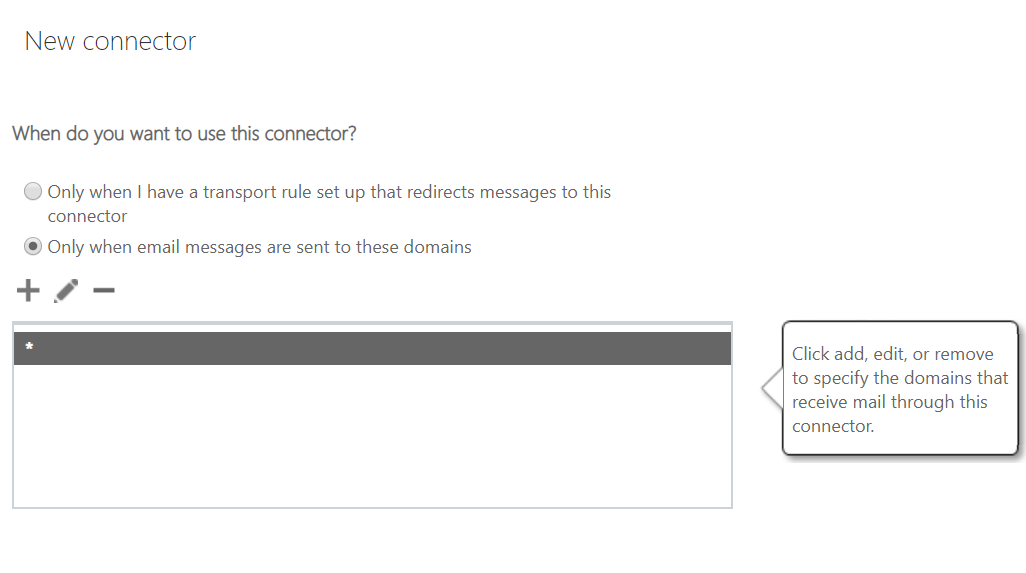
Note: Again here you can be more creative and configure a scenario where address rewriting (and more specifically here outbound email flow going via the Edge) only applies to specific destination domains – i.e you can rewrite addresses for your users but only when they email a specific partner company with a specific vanity domain
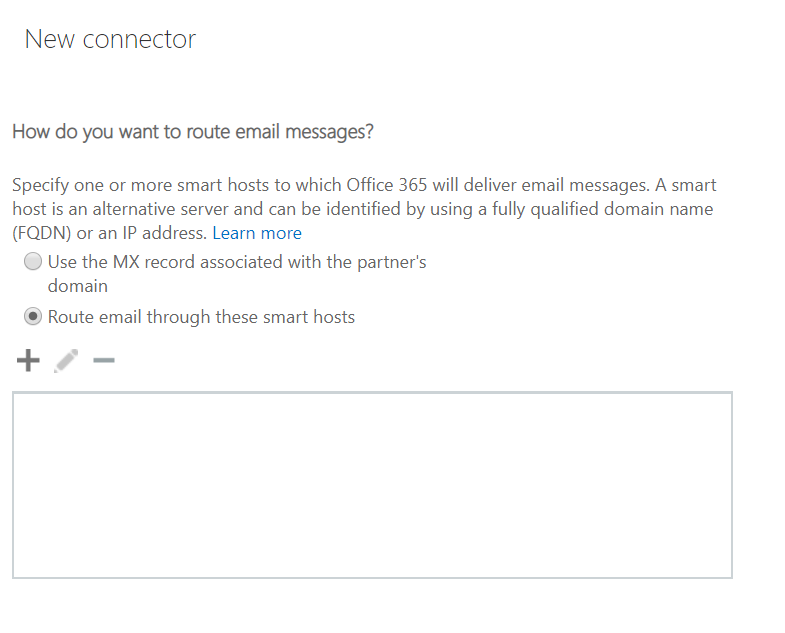
- Enter the Public IP address of your Edge Server or load balancer in front of it.
- Configure the connector to always use TLS when communicating to the Edge Server. Enter the subject name or the SAN of the certificate you will use (more on how to configure the certificate later)
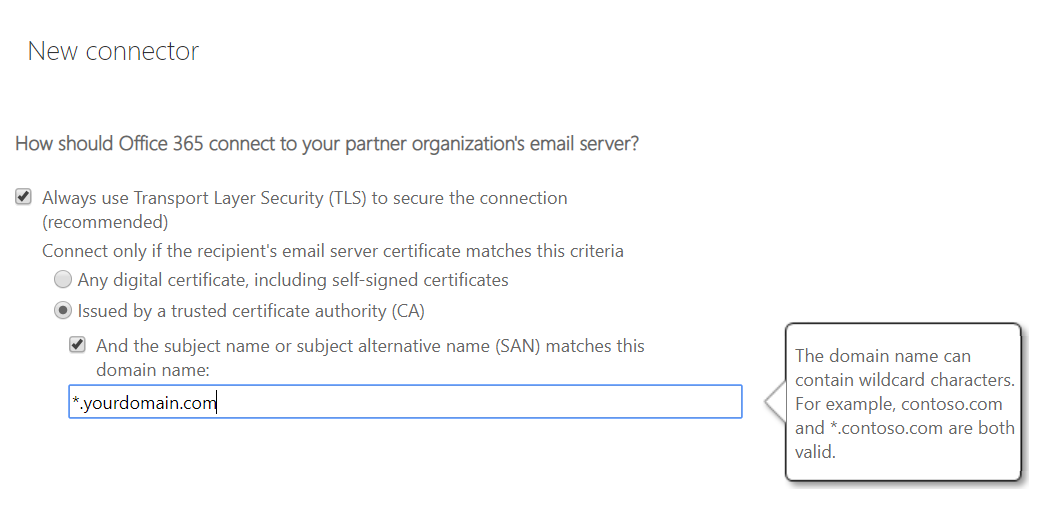
And that’s it, your outbound connector is configured in your Exchange Online tenant. If you’re configuring this in a production environment, make sure you scope it for one test user first, until you’re 100% sure the Edge Server is configured properly and mail flow doesn’t have any issues.
Don’t forget to create the connector in both tenants.
Receive and Send connectors in the Edge Server(s)
Now that we addressed the Exchange Online connectors, lets look at the next hop in the mail flow pipeline, the Edge Server.
For this scenario to work properly, three things need to be created in the Edge Server:
- Receive connector(s): This is key to accept email coming from EOP/Exchange Online
- Address Rewrite Rule(s): To be applied by the inbound and outbound transport agents and rewrite addresses
- Send connector(s): To send email outbound or inbound after the agent does its work
Lets address first the connectors.
Receive connector
There are multiple ways and scenarios to configure the receive connector, but ultimately here’s what you need to consider:
- You should create a dedicated connector that accepts connections from EOP (Exchange Online Protection) only, by using the “remoteipranges” parameter when creating the connector
- You should secure communications by adding TLS as an AuthMecanism and setting the “RequireTLS” flag to $true. You will also need to add the “TLSDomainCapabilities” and “TLSCertificateName” tags
- If in your scenario, just like in mine, the Edge Servers are stand alone, you need to make the connector ‘ExternalAuthoritative’. This is key, because for address rewriting to be executed properly, the outbound emails should be considered internal email by the Edge Server. See more on how address rewriting works in this excellent article
- Finally you need to make sure the connector accepts anonymous relay
Note: It is very important that you lock the connector down to a specific IP range and secure the communications with a certificate and TLS, since that connector will accept anonymous relay. Alternatively, if you have or can install an Edge Server in your existing Hybrid organization (and not stand alone like in this scenario), that will allow internal authenticated email, then you should opt for doing that.
Additional Note: I’ve added an additional method to protect your Edge and mail flow infrastructure from malicious relay from other Office 365 tenants. See the “Protect your Edge from malicious email relay by creating transport rules” section below.
Lets now start by creating the receive connector:
New-ReceiveConnector -Name “From EOP” -RemoteIPRanges [EOP remote Ranges] -Usage custom -AuthMechanism Tls -PermissionGroups AnonymousUsers, ExchangeUsers, ExchangeServers, Partners -Bindings 0.0.0.0:25
In the command above you should:
- Change the name of the connector as per your naming convention
- Add all EOP remote ranges that you can find here
- Define specific bindings if relevant to your scenario
Once the connector is created, we need to add the necessary AD permissions:
Get-ReceiveConnector "From EOP" | Add-ADPermission -User 'NT AUTHORITY\Anonymous Logon' -ExtendedRights MS-Exch-SMTP-Accept-Any-Recipient
Before you add TLS to the connector, you need the certificate name:
$cert = Get-ExchangeCertificate -Thumbprint [Thumbprint of your third party Exchange certificate assigned to the SMTP service]
$tlscertificatename = "<i>$($cert.Issuer)<s>$($cert.Subject)"
Note: Make sure that you obtain, import and assign a proper third party certificate to your Exchange Server Edge, before you configure the receive connector
Now lets set all the necessary TLS properties in the connector:
Get-ReceiveConnector "From EOP" | Set-ReceiveConnector -AuthMechanism ExternalAuthoritative, Tls -RequireTls:$true -TlsDomainCapabilities mail.protection.outlook.com:AcceptOorgProtocol -TlsCertificateName $tlscertificatename -fqdn mail.yourdomain.com
Make sure that the FQDN of the connector matches the certificate name.
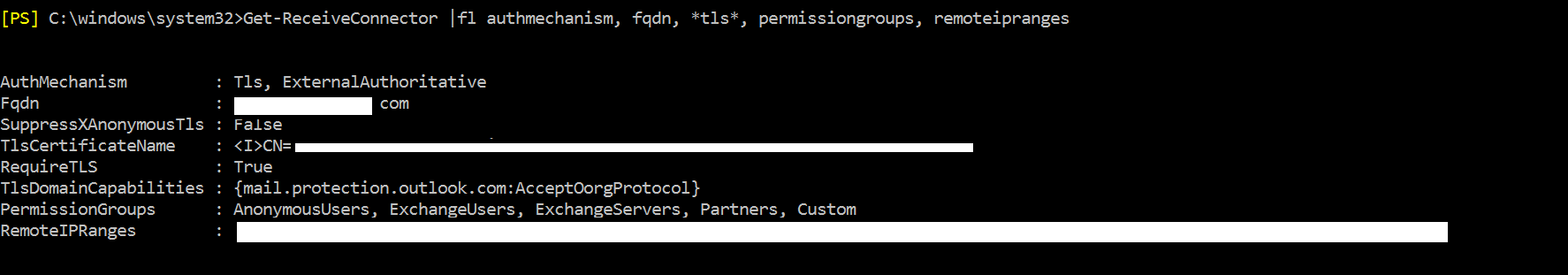
Above a snapshot of the most relevant properties of the receive connector.
Send connector
Again here, for the send connector, you can have multiple scenarios. For mine, my Edge Server just has a simple send connector, not scoped to any transport rule or address space, that sends outbound email for all domains. Since this send connector is to send email to the Internet, no special TLS settings are configured.
The command I used was:
New-SendConnector -Internet -Name "To Internet" -AddressSpaces *
See here how to create a send connector and create your own.
Exchange Edge Address rewrite rules
Before I explain what rules you should create, I strongly encourage you to read this Address Rewriting on Microsoft Edge Servers article.
Address rewriting rules can be done per domain or per user. When you plan yours, think about if a domain type rule is enough or not, i.e do you want to translate John@abc.com to John@xyz.com, or do you want to translate John.Smith@abc.com to JSmith@xyz.com, meaning is the prefix changing or not? If the answer is yes the prefix will change, then you need one rule per user.
Lets now check what we need to do for this specific scenario:
- John.Smith@tenant1.myexchlab.com is on the first tenant and we need to translate his address to John.Smith@myexchlab.com
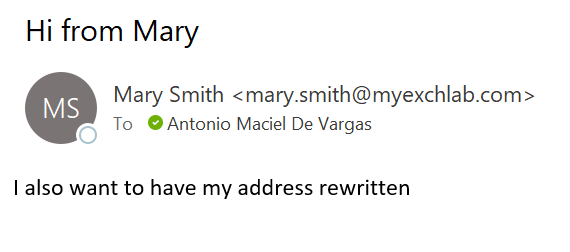
- Mary.Smith@tenant2.myexchlab.com is on the second tenant and we need to translate her address to Mary.Smith@myexchlab.com
Now the rules:
New-AddressRewriteEntry -Name "John tenant1.myexchlab.com to myexchlab.com" -InternalAddress John.Smith@tenant1.myexchlab.com -ExternalAddress John.Smith@myexchlab.com
New-AddressRewriteEntry -Name "Mary tenant2.myexchlab.com to myexchlab.com" -InternalAddress Mary.Smith@tenant2.myexchlab.com -ExternalAddress Mary.Smith@myexchlab.com
The rules I created in this scenario are bi-directional.
Again you should consider per domain rules when applicable. You can also import the rules via CSV, to make sure you can create all rules with minimum effort.
Protect your Edge from malicious email relay by creating transport rules
When you set up the connectors for inbound and outbound relay of email, although the connections require TLS and only accept emails from Exchange Online, you have no control on what other Exchange Online tenants will try to do, and if they try to use your Edge to relay email.
To be able to control that, you need to create multiple transport rules in all of your Edge servers. Creating a transport rule in an Edge server is not as linear and doesn’t have the same available options that a CAS server has, but here’s what you need to do:
First exclude the recipient domains by creating one transport rule for each (or consolidating all in one) that basically stops transport rule processing if it finds a match:
New-TransportRule -Name "Emails from Outside to myexchlab.com Inside" -FromScope NotInOrganization -AnyOfRecipientAddressContains "myexchlab.com" -StopRuleProcessing $true
New-TransportRule -Name "Emails from Outside to tenant1.myexchlab.com Inside" -FromScope NotInOrganization -AnyOfRecipientAddressContains "tenant1.myexchlab.com" -StopRuleProcessing $true
New-TransportRule -Name "Emails from Outside to tenant2.myexchlab.com Inside" -FromScope NotInOrganization -AnyOfRecipientAddressContains "tenant2.myexchlab.com" -StopRuleProcessing $true
And finally the rule with less priority that will drop the email if it’s from outside of the Organization:
New-TransportRule -Name "Drop email if Outside of Organization" -FromScope NotInOrganization -DeleteMessage $true
The rules above must be in the right priority, meaning priority 0 to 2 should be to the rules that stop processing more rules, if an internal domain is detected.
Then, if there’s no internal domain detected in any of the recipients of the message, the Edge should drop the message. This is to allow that inbound email still works and outbound doesn’t allow malicious connections for relay.
Basically what you are saying in the last rule is that if the sender is not internal to your organization, have the Edge server just drop the email, if that rule ends up being processed. I strongly advise you to test the rule right after you implement it, and make sure it allows all the domains you need.
Lets show the rule in action:
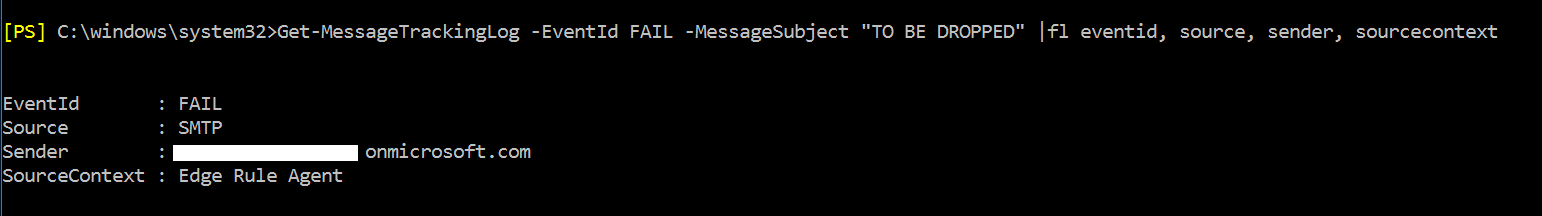
As you can see above the email sent from a non accepted domain gets dropped by the Edge server. Also remember that the rules was processed because no other rule found a domain match in all recipients.
Consider the transport rules, although unfortunately very limited when applied in Edge Servers, when it comes to available actions and predicates, as an additional and important layer of security that you can apply to your infrastructure.
Accepted domains in the Edge Server
One of the important things I mentioned before, is that the Edge Server considers the outbound and inbound emails, sent to and from the domains you are translating to and from, as internal emails.
In my scenario all I had to begin with was a stand alone Edge Server, with no accepted domains, which might not be the case for you if you use an Edge in an existing Hybrid infrastructure, but if it is, here’s what you need to know about accepted domains:
- Add the vanity domain from source and destination tenants, that you are translating from (outbound) and to (inbound)
- Add the vanity domain both tenants are sharing
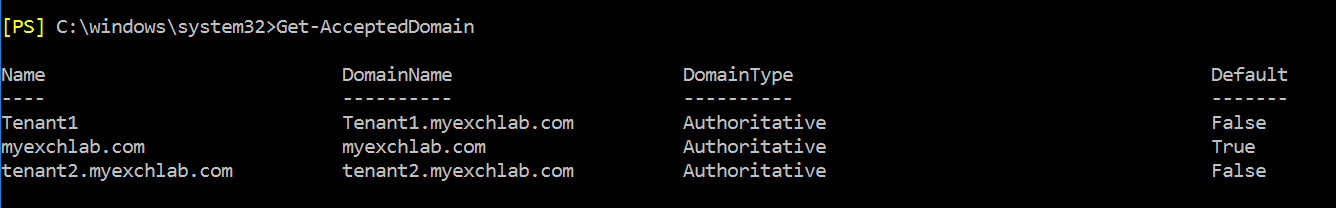
Here’s the snapshot of mine, just so you understand better what I needed for my scenario.
DNS Records
Now let me describe how my email related DNS records should be configured. Remember this is specific for my scenario. Also I am only covering the MX and SPF DNS records. Make sure that you apply the industry recommendations for email when configuring your email domains (i.e DKIM).
The MX records
Here’s how the MX records for all 3 domains are configured, in my scenario:
- tenant1.myexchlab.com: MX record points to EOP in the Office 365 tenant where the domain is valid
- tenant2.myexchlab.com: MX record points to EOP in the Office 365 tenant where the domain is valid
- myexchlab.com: MX points to the pool of Edge Servers
The explanation for the above is simple, you need to make sure that any email outside of the address rewriting can go to the correct recipient. For example, if someone external emails Peter@tenant1.myexchlab.com, there’s no reason for the email to go via the address rewriting process or the Edge pool. And this applies to any external communication going to source and destination going directly to those domains.
As for the myexchlab.com, the opposite happens, meaning if someone emails Jack@myexchlab.com, the email must go to the Edge just so the inbound transport agent can translate that address to Jack@tenantX.myexchlab.com. For that reason and because the Edge is the source of authority for the myexchlab.com domain, that effectively is not an SMTP address in any recipient in my scenario, the MX for that domain needs to point there.
The SPF records
Here I opted for the safest approach and configured all SPF records the same way, for all 3 domains, to include senders from:
- MX record
- Exchange Online protection
- The Edge server
Lets break this down:
- tenant1.myexchlab.com and tenant2.myexchlab.com: for this domains, hosted in Office 365, allowing the MX and EOP is redundant but it does no harm, and I allowed the Edge server for one simple reason, if the address translation fails for some reason, the email can still go from the Edge server outbound and the source address would be on of these domains, so for those unexpected scenarios you should add the Edge to the SPF.
- myexchlab.com: for this domain, adding EOP is in fact not needed in my scenario, since there’s no point in time where the domain is expected to be moved to Office 365, but in most scenarios, specially migration scenarios, EOP should be in the allowed senders, so I added it. The Edge and the MX are again redundant, but you should have at least one of them.
Here’s how the SPF would look:
v=spf1 mx ip4:[Edge IPV4 Public address] include:spf.protection.outlook.com ~all
How everything works
It’s time to test the scenario now. Here’s what I will do:
- Send an outbound email from both tenants
- Reply to the outbound emails
- Send an inbound email to both tenants
The results we will analyze are:
- Verify source and destination “from” and “to” addresses, looking at the email in the destination
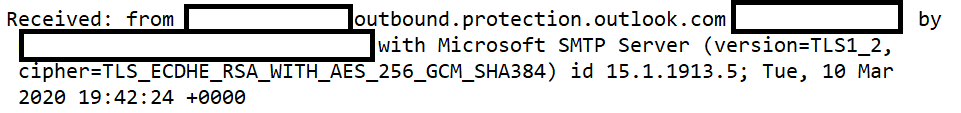
- Verify that TLS is being used
- See the transport agents in action
I don’t want to prove my scenario with screenshots, since I don’t think that’s relevant and I’d have to grey out most of the information anyway, but below you can find some snippets of how it worked, just so we’re clear on what you should expect and also how to troubleshoot any issues.
Outbound email from both tenants
The email being sent at the source, from John:
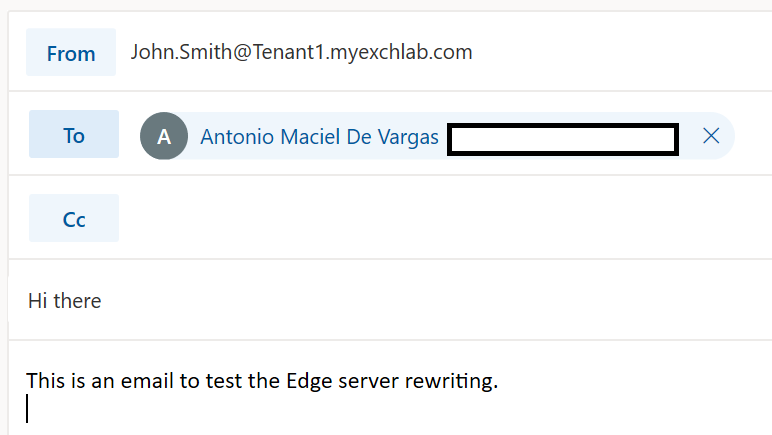
And from Mary:
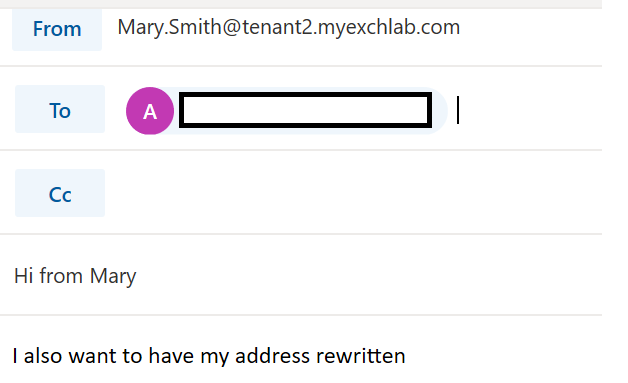
Now lets see what happens when the email hits the Edge server:
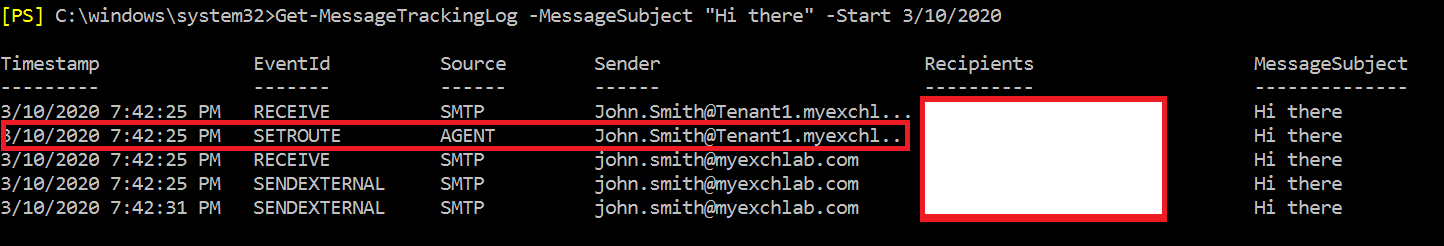
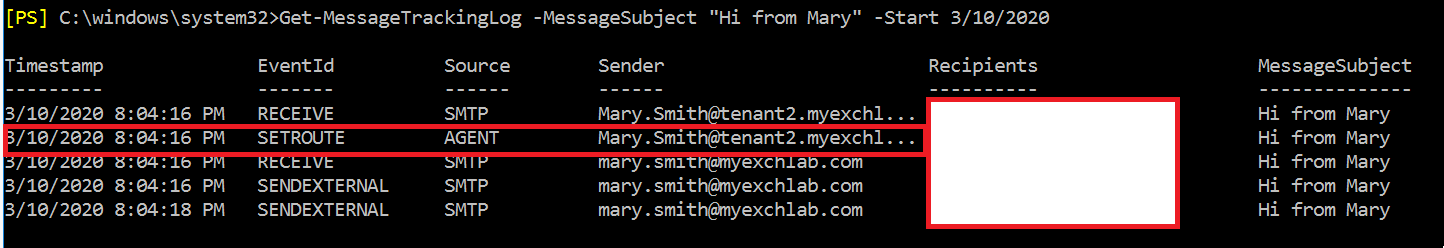
I used the message tracking log, and as you can see for the message I sent, the agent event “SETROUTE” is translating the address.
Lets look at the message in the destination:
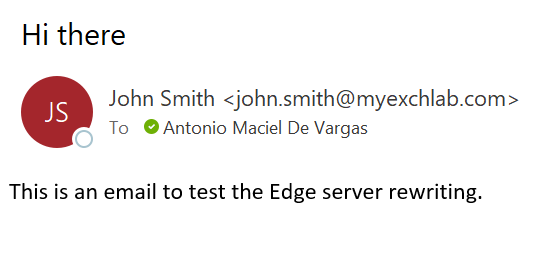
… and now lets really look inside the message 🙂 (just one of them now)
The original mailfrom address:

The address translated:
And TLS being used:
Reply to the outbound emails
For the reply I will just use one user as the example, since the behavior is the same for both.
So lets see what happens in the Edge:
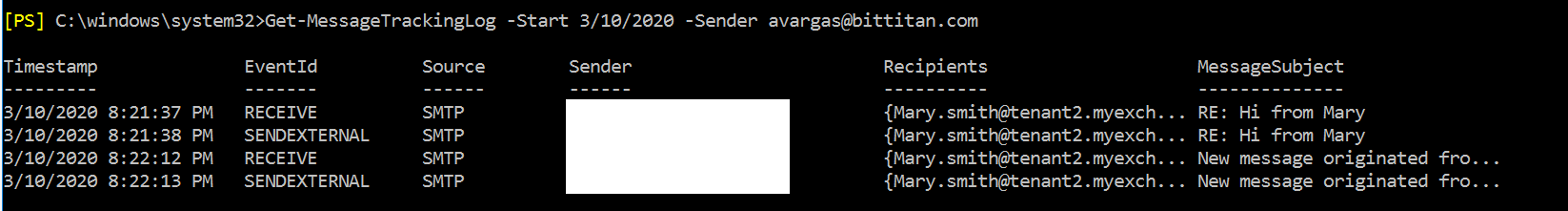
As you can see above, there’s two messages address to Mary, one is a reply and the other a brand new message, in both cases you can see that the recipient got translated. Unlike outbound email, you won’t see an event ID associated to the transport agent, but you can check in the recipients column that it did its job.
And finally, the external email in the internal mailbox:
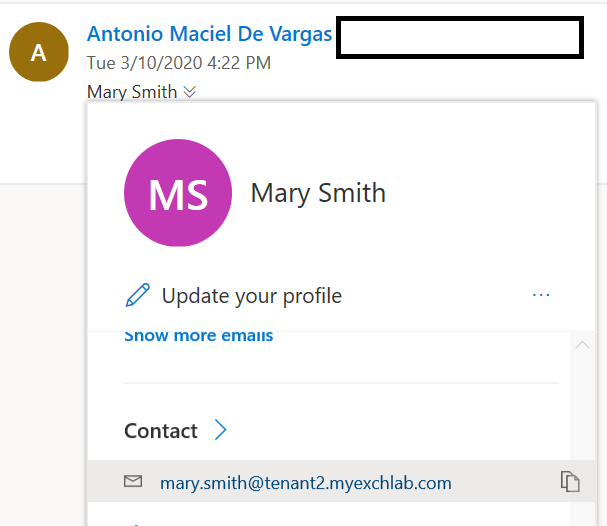
That’s it. Enough screenshots. Hopefully you understood how everything works and how you can troubleshoot it.
The bottom line
Hopefully after reading this blog post, you can understand better how the mail flow coexistence can be done. This was in fact a simple scenario but more will come in future posts. If you want me to describe and blog about a specific scenario you have, or if you need help understanding it better, please drop me a line.
I’ve been working in the migration business for more than 5 years now, and I’ve seen a lot of partners and customers that do need mail flow coexistence between two tenants. Because it’s not simple for Microsoft to address that, and allow things like the same vanity domain in two tenants, some companies created products and services that try and fill that gap, but like I said previously in this post, handing over your mail flow pipeline is not a simple decision nor one that Enterprises are willing to take, specially when it’s not that hard for you to do it yourself and I am sure that building and maintaining a high available mail flow infrastructure (like Edge servers) is cheaper than paying a per user fee to get this functionality.
In fact, for many Enterprises, they already have what they need. This doesn’t necessarily has to be done with Edge servers. The top email appliances in the market can do this as well. I might include some of those scenarios in future posts.
Stay tuned and thank you for reading!