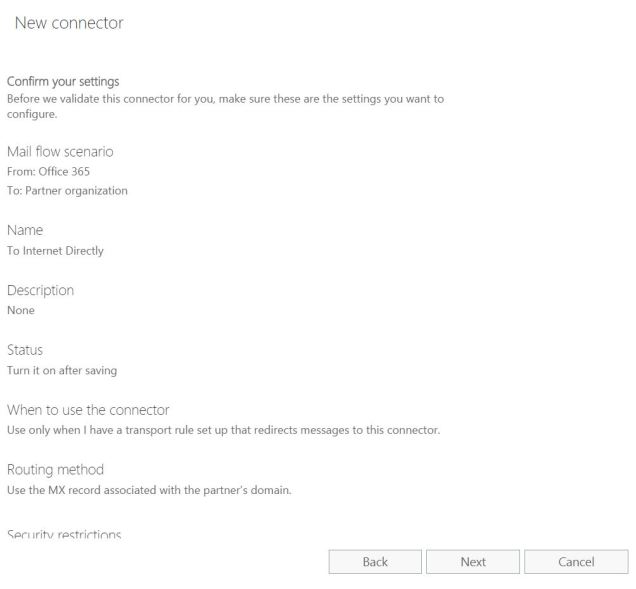
Just recently and when helping drive a Google Suite to Office 365 e-mail migration, I was faced with a problem that affected my mail routing capabilities between the 2 systems: Not all mailboxes in Office 365 had the @tenantid.onmicrosoft.com domain.
Now that can be a problem, specifically because in many coexistence scenarios (including the one I mentioned above), that “tenant.onmicrosoft.com” or the “tenant.mail.onmicrosoft.com” address is used as the forwarding address on the e-mail system coexisting with Office 365.
Here are a couple of articles describing cases where the service or mail routing domain were missing:
User@Domain.onmicrosoft.com disappeared
The main problem in this cases is that you can find that some users don’t have that address, as an additional smtp address, the hard way, which basically is getting an NDR on the source system when it tries to forward that email to Office 365. So to be on the safe side, and because this happened to me a few times, I decided to create a script that identifies all users that don’t have an address from a specific email domain.
Some bullet point instructions for the script:
- you can download the script here
- The file you downloaded contains 2 scripts: Export-UsersNoOnMicrosoftAddress.ps1 and Log_Functions.ps1. Copy both into the same folder
- Open a PowerShell window and run .\Export-UsersNoOnMicrosoftAddress.ps1
- The script will prompt you to enter your Office 365 credentials
- The script will prompt you for an email domain (i.e tenant.onmicrosoft.com)
- All users that don’t have an address with that email domain will be exported to a file called UsersNoOnmicrosoftAddress.csv located in the same folder
- A log file called ExportUsersOnmicrosoft.log is also created in the same folder, where you can check for any errors after running the script
See screenshot below with the output of the script on the console:
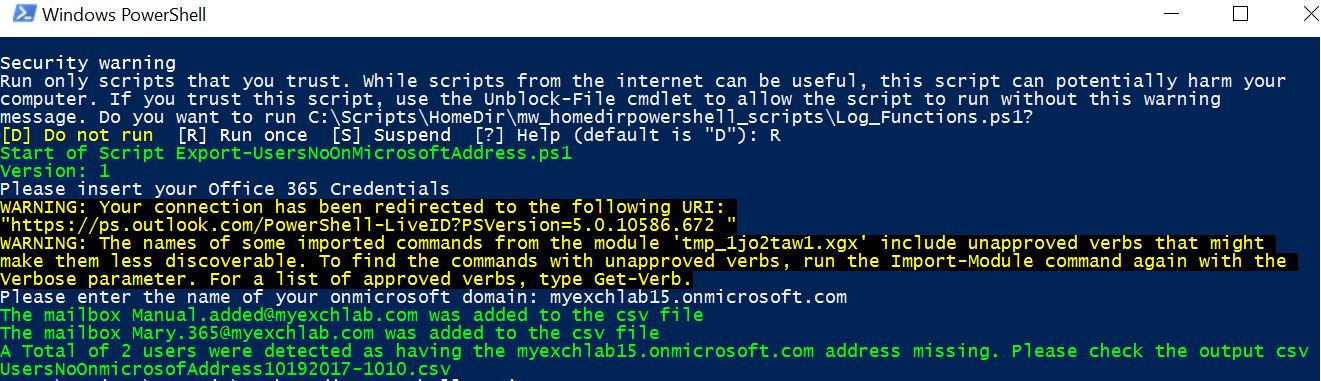
Of course that, if you look at the code, you will easily realize that the script can export users that don’t have an address from any domain you chose. That being said use it as you see fit. To me it helped me a lot on detecting the users with the problem described above.
Just a quick note before I finish this post: there are 2 reasons for this script not to fix the problem, adding those addresses:
- AD Connect: blocks you from adding the addresses directly in 365, meaning you will need to resolve the problem on premises and force a sync of the new addresses to 365
- Email address policies: it’s ultimately the best way of resolving email address problems in bulk, so that’s the route you so use
As always if you have any questions let me know. Enjoy.